Password spray attacks on accounts have increased rapidly in recent months. As a result, the security risks for accounts that do not use MFA for authentication have increased significantly. Microsoft works in the past on different ways to enable MFA for all users they work with Azure and Microsoft 365. One first try was the activation of security defaults, but this can be deactivated by user.
Based on this development and for other reason Microsoft announced the enforcement for Mutlifactor authentication for all sign-in/access to the Azure Portal. This announcement was a little suprise and bringe some challenges to organization espesically when we take a look at service principals and break glass accounts. Don´t get me wrong, it is mandatory to enable MFA for all users they access your tenant and have a valid and regulary reviewed Conditional Access policy in place. But for some special accounts this was not the focus or recommended. In this article I will explain how Microsoft rollouts this enforcement which steps you have to proof and how you can ensure that you are not affected or prepared for the upcoming changes.
Contents
Timeline
Microsoft announced in May with the blog post from Erin Chapple the change in orientation and the announcement of the MFA for all accesses to the Azure Portal. The first announcement contained general information, but less information on how this will be implemented and for which types of accounts this will be the case.
End of June Microsoft released additional information about how they will enforce the MFA for the Azure portal access with the Updated blog article on MFA requirements.
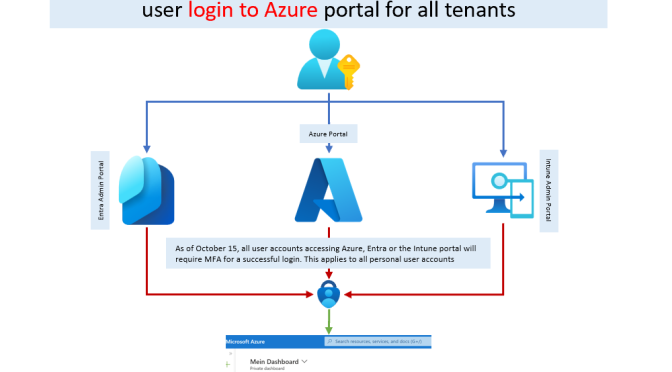
- Beginning of July 2024 Microsoft will starts rollout the MFA enforcement for all existing tenants. The enforcement will only affect sign-ins for Azure Portal access, Entra Admin Portal and Intune Admin Portal. No other access ( via Powershell, Azure CLI, etc.) will be affected.
- The configuration will come into effect (for most customers) on October 15. Most customers have received this information via Mail as the activation date
- Starting in early 2025 Microsoft will extend the enforcement for all sign-ins including Powershell, Azure CLI, etc.
Realization
It is important to understand that this enforcement is mandatory and can not be disabled. In the rollout phase you can postpone the activation (will be described later in the article) but it will affect your tenant latest in 2025. The MFA requirement affect user access to the Azure portal, MS Entra admin center or the Intune admin center.
No Conditional access policy will be applied
The MFA enforcement will not be realized via Conditional Access policy. Which means you does`nt see this MFA enforcement listed in the Conditional access policies.
There is a simple reason for this. Conditional Access requires an Entra ID P1 license or above. The requirement for Azure MFA will be enforced regardless of whether a corresponding license is available.
The implementation will be enforced on top of any existing Conditional Access Policy. Which means after the change is activated on your tenant it will be mandatory for all user sign-ins. It will be enabled based on the Microsoft Entra sign-in logs. This can be used to filter login types and accesses and is therefore the ideal way to enforce MFA for certain user logins and accesses.
Preparation
It is important to prepare for this upcoming change. Microsoft will notify all Tenant owners via E-Mail and through Azure Service Health notifcations 60-day in advance. The are some important steps for preparation
- handling of MFA requirement for break glass accounts
- overview of users who do not require MFA when logging in
- handling of service accounts that are used in Azure resources
Handling of MFA requirement for break glass accounts
In my Azure governance and security workshop, I recommended the need for an emergency account called a Breakglass account every time. I followed the best practice of setting up Breakglass accounts without MFA (in case the service is unavailable, signing in is always possible). The Break glass accounts are user accounts and directly affected through this change.
There are several MFA methods available for breakglass accounts, but recommendation is to switch to phishing resistant MFA via FIDO2 keys. This enure high security for this high privilged accounts and is easy to manage at the same time. In the following article Howto setup and monitor Break Glass Accounts in your Tenant I reflect the changes to setup breakglass accounts with FIDO2 keys.
Overview of users who do not require MFA when logging in
In general it is important that all users in your tenant using a second factory for sign-ins. There are several options available to enforce the use of MFA in your tenant. From use of Authenticatior app over Windows hello for Business through Device compliance via Intune. All this different ways can be setup via Conditional access. So please ensure that all your users are affected from at least one Conditional access they enforce the need for MFA. Or ensure that you have a valid Conditional access strategie in place. When you interested to learn more about Entra ID security, please take a look at our Cloud Identity Summit 2024. The conference is a free hybrid event, where we will share many information about Identity Management and Identity Security.
Note: If MFA is already set up for all your user and service accounts – e.g. through Conditional Access – the activation of MFA enforcement for logging into the Azure portal is transparent and has no effect.
Handling of service accounts
If you current use user accounts as service accouns for scripts, automation or something else – this accounts will be affected from the MFA enforcement. It is not recommended to use in-person accounts as user accounts. So ensure that you doesn`t use user accounts as service accounts. If this is the case it is important to switch to workload identities like managed identities or service principals.
Microsoft information
Microsoft starting to inform the tenant owner about the upcoming, breaking changes via E-mail. In the last couple of days you have received the following mail:
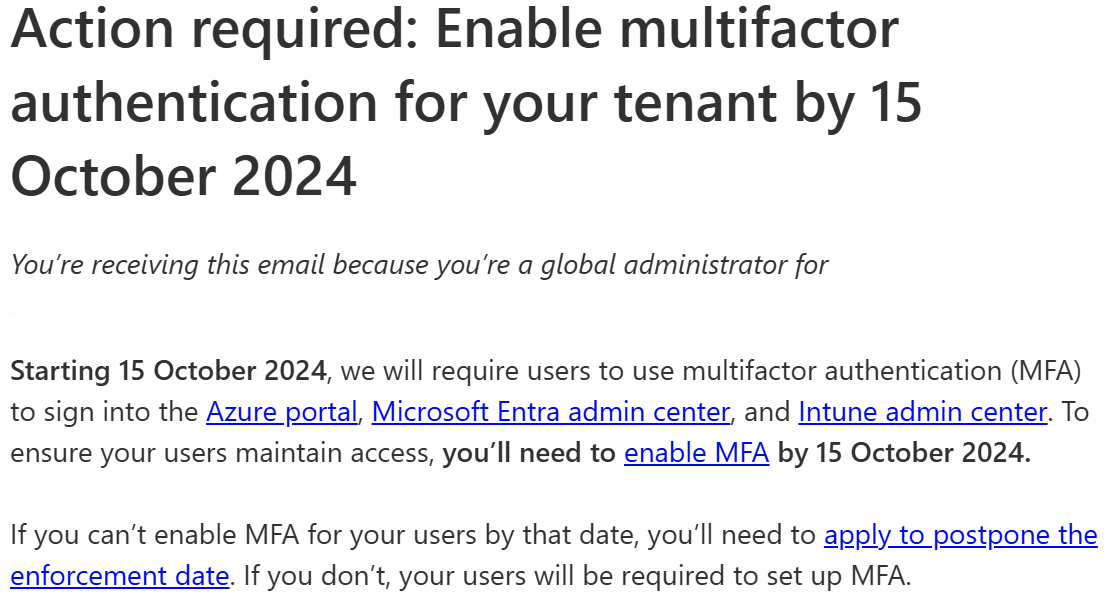
You will also notified via the Azure Portal when you access the portal you get an hint about this change. On this link you will redirect to the follwoing landing page
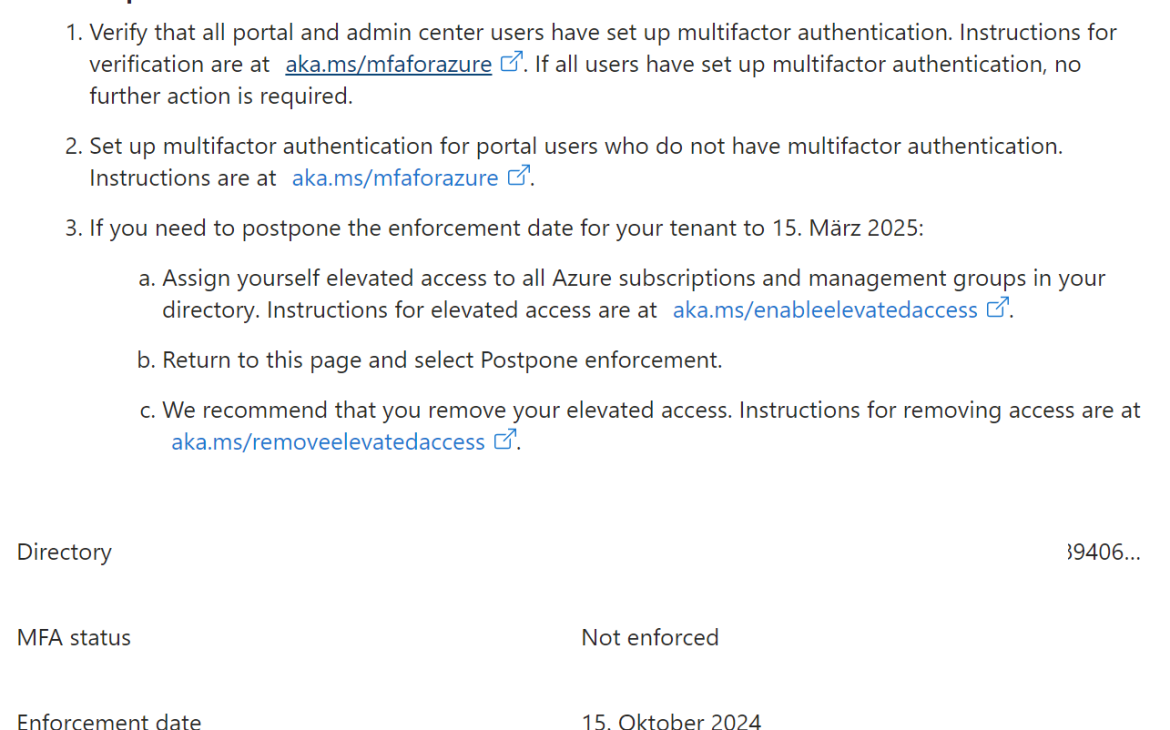
Here you have the option to postpone the activation one time, but I really recommend to work on the MFA requirements and to avoid to use the postpone option.
Note: The postpone option is only possible for one time and the activation will take effect beginning of 2025. It is possible that the activation directly will be enforced for portal access and azure cli access.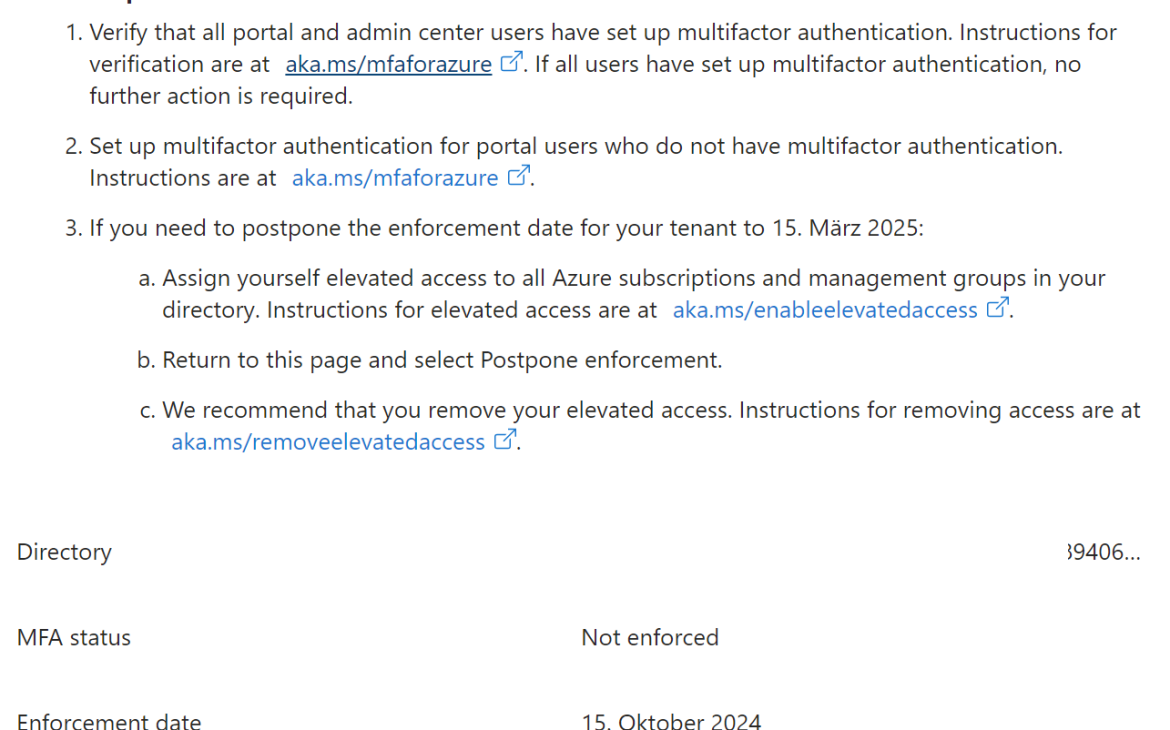
Conclusion
There are still some time to react to this changes and the timetable should look like this:
- ensures that the break glass accounts are secured by MFA (preferably using FIDO2 keys)
- ensures that no user accounts are used as service accounts and, if they are, migrates them to service accounts or workload identities
- check your conditional access strategy and that it enforces MFA for all accounts or start using conditional access
- If you want to learn more about Cloud Identity Management and Security, register for our free hybrid Cloud Identity Summit on 05.09.2024

Links
- Microsoft will require MFA for all Azure users
- Update on MFA requirements for Azure sign-in – Microsoft Community Hub
- Sign-in logs in Microsoft Entra ID – Microsoft Entra ID | Microsoft Learn
- Howto setup and monitor Break Glass Accounts in your Tenant
- Introduction to securing Microsoft Entra service accounts – Microsoft Entra | Microsoft Learn
- Cloud Identity Summit – Hybrid Cloud Identity Conference