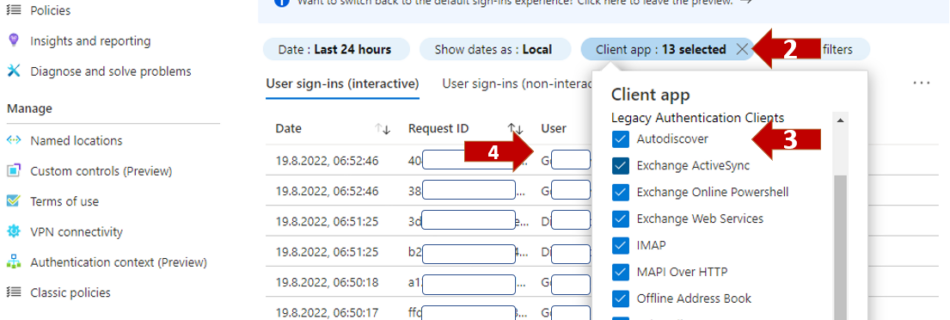
Speaking at Infinity 365 in Salzburg about Entra ID and Conditional Access Security
The Infinity 365 conference was born as a Sharepoint conferencen and growths over the years to a big Microsoft 365 conference in Austria. I´m really happy to be invited to this great Microsoft 365 conference and get the opportunity to held two sessions about Microsoft Entra ID. Zero Trust starts with Entra ID In today’s …