Microsoft model for a scalable Cloud Adtoption is based on the Enterprise Scale Architecture and I think this is a scalable and useful modell for every customer that uses Azure ressources. It´s based on the definition to granulary devide the workloads in different subscriptions and gives via Management Groups the possibility to group this differnent subscription into workload groups like Development, Core, etc. I know many customers struggle with this model and mistakenly think that Enterprise Scale is a reference to Enterprise customers, but this is not the case.
Based on the Enterprise Scale Architecture some services and security features can only be activated on subscription level to guarante that each resource inside the subscription is secured. This basis makes it even more important for customers to consider the Enterprise Scale Architecture or to orient themselves towards it.
The Microsoft Defender for Cloud and especially the Defender for Server P1 and P2 plans can only be activated on subscription level in the past. Microsoft has decided to change this and now allow plans to be activated at resource level (per server). It is important to understand that the principled approach activating on Subscription Level and the Enterprise Scale architecture are still valid and needed and this possibility is only a concession to cover certain requirements:
- manage security configurations at a lower hierarchy level
- flexibility for excluding specific resources (VMs) inside the subscription
- enable different plans on subscription because for implementation of Enterprise Scale approach
Contents
Scenarios which are covered
With this feature Microsoft allows the following settings inside a subscription for Defender for Server plans:
- Enable / Disable Defender for Servers Plan 1 at resource level
- Exclusively disable Defender for Server Plan 2 at resource level
- Both plans – enable P2 at the subscription level and downgrade specific resources for P1 – the other way is currently not possible
Effect on MDE deployment after activation
- Including VMs in Servers Plan 1 will trigger automatic deployment of Microsoft Defender for Endpoint (if not already deployed)
- Excluding VMs from Servers Plan 1/Plan 2 will also exclude from deployment of Microsoft Defender for Endpoint (if not already deployed)
Notes
- Activation is only possible via API (currently no GUI)
Once the settings have been changed at resource level, the resource no longer inherits any settings from the parent subscription until the configured settings are deleted
Working with the API to get, update and delete the Defender for Servers plan on a specific resource via PowerShell
Here are some examples how to work with Powershell to get, update and delete the Defender for Server plan on resource level. I make some snippets on each topic and share the script in my Github repository
The overall script needs some default lines :
# Variables to access Azure environment
$subscriptionid = “00000000-0000-0000-0000-0000000000000”
$resourcegroup = “Name-of-resourcegroup-contained-the-server”
$vmname = “AzureServerName”
$url = “https://management.azure.com/subscriptions/$subscriptionid/resourceGroups/$resourcegroup/providers/Microsoft.Compute/virtualMachines/$vmname/providers/Microsoft.Security/pricings/virtualMachines?api-version=2024-01-01”
Get an set access token for access via REST API
$accessToken = (Get-AzAccessToken).Token
$headers = @{“Authorization” = “Bearer $accessToken”
“Content-Type” = “application/json”}
Prepare API request to set Defender for Server plan 1 on selected VM
$body = @{ location = $location
properties = @{pricingTier = “Standard” subPlan = “P1”}
} | ConvertTo-Json
Get status of Defender for Servers P1 or P2 on specific resources via PowerShell
Invoke-RestMethod -Method Get -Uri $url -Headers $headers | ConvertTo-Json
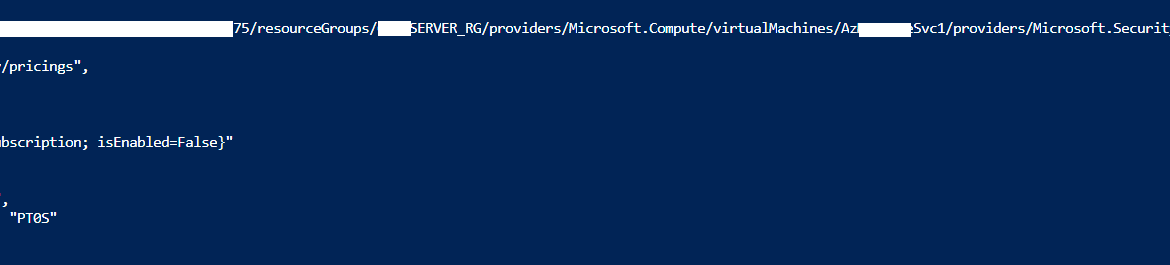
Enable Defender for Servers P1 on specific resource via PowerShell
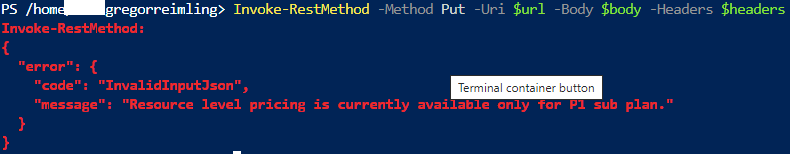
Invoke-RestMethod -Method Put -Uri $url -Body $body -Headers $headers | ConvertTo-Json
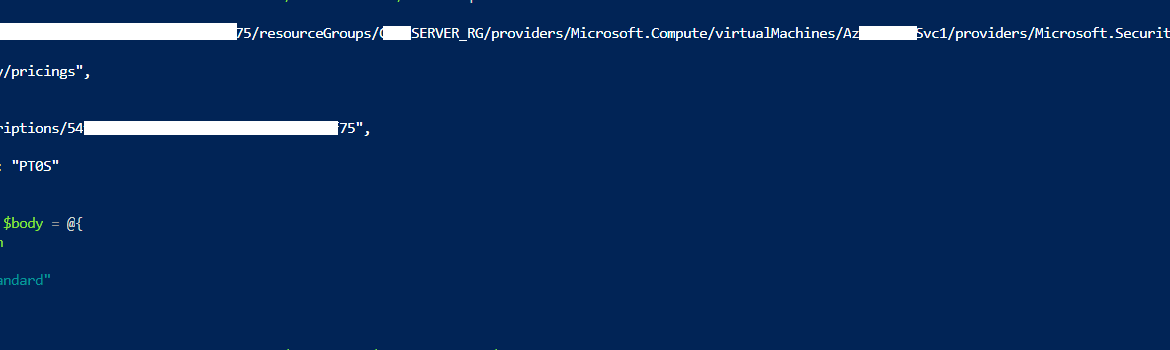
Enable Defender for Server P2 on specific resource is not possible
Enablement at scale
Tom Janetscheck created a Powershell script which allows to activate the plan for all Servers inside a speficfic resource group or via Azure tags.
- Download the file and save it as Powershell
- Select wheter you set pricing by tag or by resource group
- Follow the script instructions
Conclusion
The new possibility to enable Defender for Servers at resource level is a great way to improve security for resources the reside side by side in Test environments or to improve security for Servers in SMB subscriptions. Please note that the principled approach activating on Subscription Level and the Enterprise Scale architecture are still valid and needed and this possibility is only a concession to cover certain requirements.
