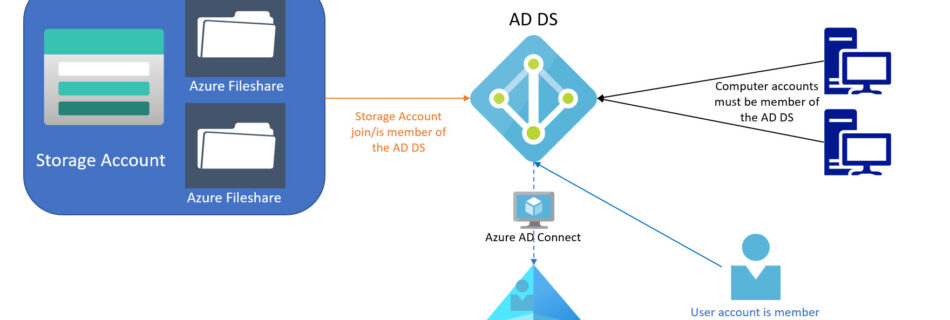
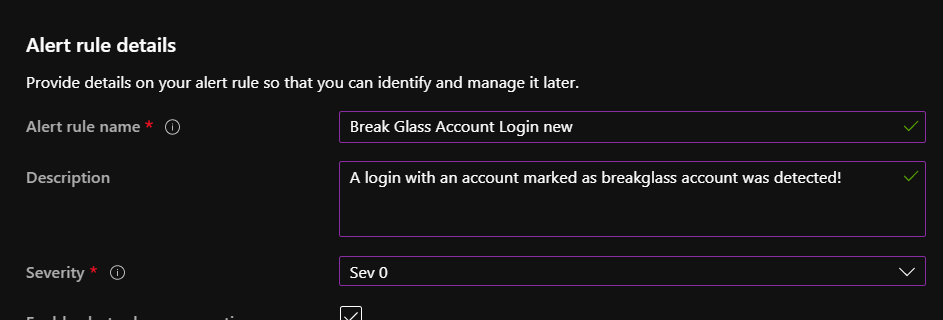
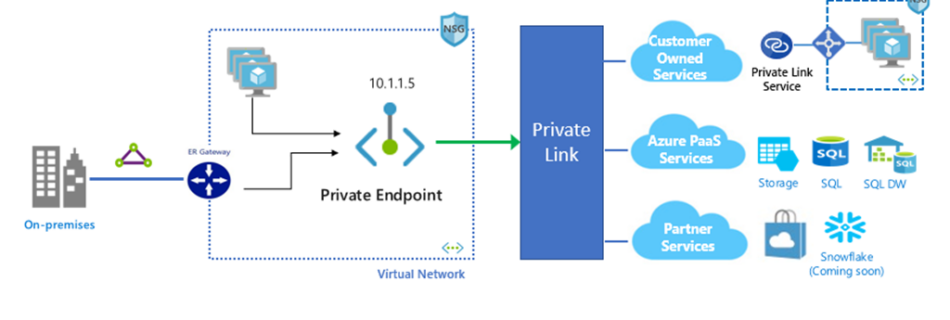
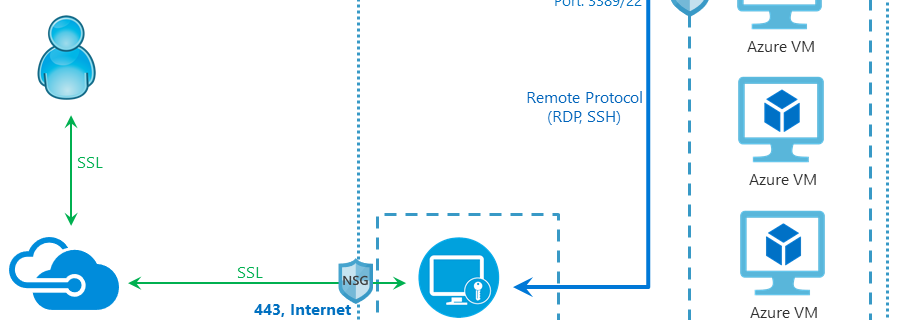
Azure VM Best Practices
Last year Gregor Suttie and Richard Hooper launched the Azure Advent Calendar and I got to support with a session on Azure Bastion. This year they improved on the idea with the Festive Tech Calendar. I’m happy to be back with an article on Azure VM best practices. I hope you find the article helpful …