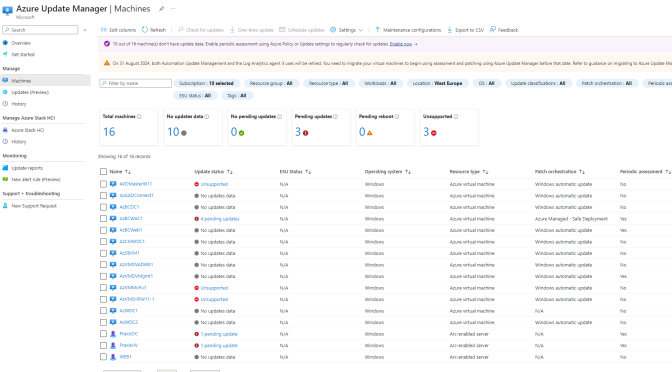
In the first part of this article (Three-big-reasons-to-migrate-to-update-manager-and-forget-the-classic-update-management-center) I dived into the improvements and reasons why Micrsoft introduce Azure Update Manager as a successor of the classic Update Management Center solution based on Azure Automation. In this part, I will explain how it works and what major improvements and new functions the Azure Update Manager offers
Please note: Azure Update Center is based on Azure Automation and needs the Microsoft Monitoring Agent. The MMA has been discontinued and will no longer be supported after August 2024. Support for Update Center has therefore also been discontinued.
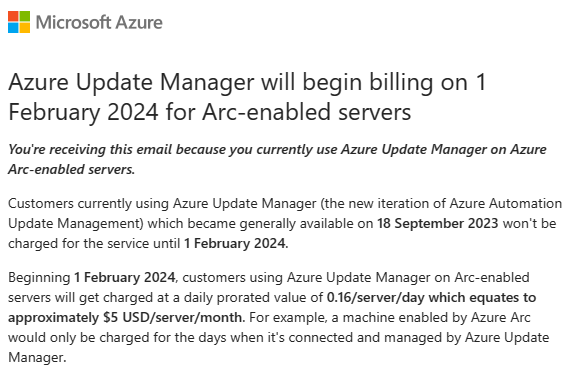
2nd note: Microsoft will charged at a daily prorated value of 0.16/server/day which equates to approximately $5 USD/server/month beginning 1 February 2024 for customers using Azure Update Manager on Arc-enabled servers.
Contents
Activation and configuration of Update Manager
As you can see there are many options available, but it can be grouped in some categories based on the Operating system and that is in use.
To activate the new Update Management solution we have to register the planned VMs in the Update Manager to enable the management over this solution. One of the integral shift away from the classic Update Center solution is the natively integration into Azure Arc. Therefore Update Manager can now enabled via Azure Policy which means the selected Policy can enrolled via the Enterprise Scale approach on Management group, subscription or resource group level and all servers inside the selected hierarchy get note from the Policy configuration and will be registerd in Azure Update Manager.
Setup Azure Policy initiative
To enable Update Manager best way is to create a Azure Policy initiative. A initiative in Azure Policy defines a group of different policies. This is best way to initialy group all Update Manager policy into one single group.
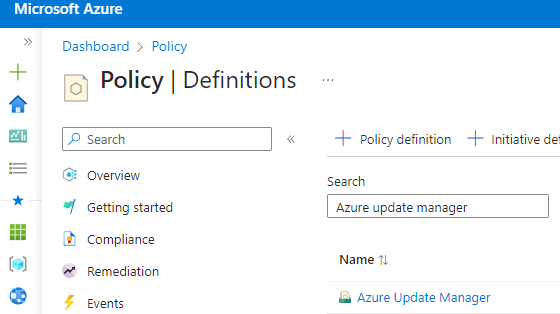
Add the following policies In the intiative:
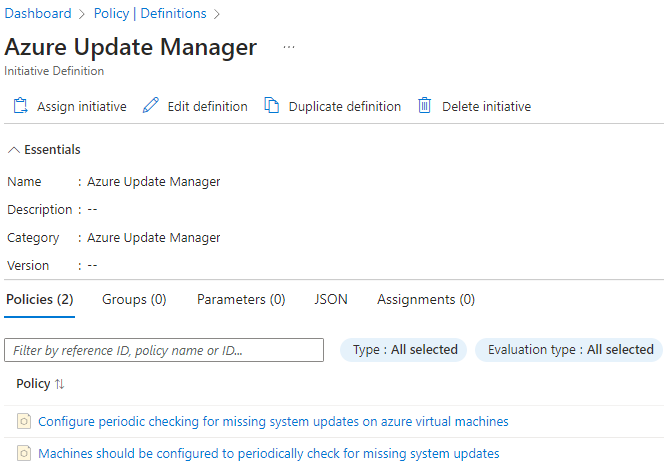
- Configure periodic checking for missing system updates on azure virtual machines
- Machines should be configured to periodically check for missing system updates
Please note: Is Update Manager planned to used for Azure Arc machines, it is recommended to create another initiative for Azure Arc machines in order to be able to control the possible patch orchestration options (see next chapter) individually.
The created initiative can be assigend at Management Group, Subscription or Resource level.
Patch orchestration options
Before deploying the Azure Update Manager solution it is important to understand the different patch orchestration options that this solution provides and are part of the big improvements. As of now AUM offers five different patch orchestration options:
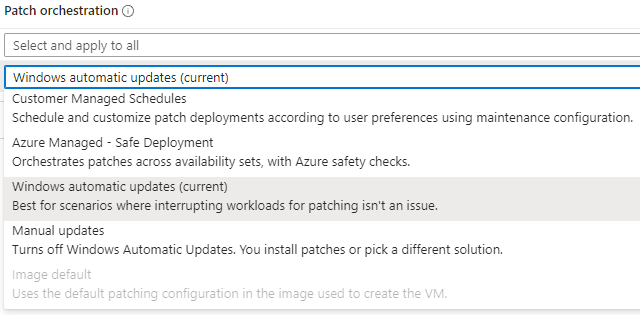
I will explain the different options below.
Customer Managed Schedules (Preview)
With this option you can configure maintenance windows based on your selected VMs. The VMs can selected with a dynamic scope editor inside the Maintenance configuration, where you can edit the scope on the following different options:
- Resource Groups
- Resource types (Azure VMs and Azure Arc enabled Servers)
- Azure Regions
- OS types (Windows or Linux)
- Tags
I recommend to create Maintenance windows based on the last criterias without using Resource Groups. Through these options, there are multiple ways to set up maintenance slots for servers across subscription boundaries. It also shows how important Azure governance is, as tags come into play here again – and a good tagging strategy is essential for an easy-to-manage Azure environment 😉
I recommend to create an additional resource group, because created Managed schedules will created as resource in Azure and it make sense to store this centrally for all things related to Azure Update Center.
Azure managed – Safe deployment
This is for me the most exciting new feature and at the same time long overdue 😉
With this option, Azure orchestrates the updates for the selected VMs, taking into account criteria such as Availability Sets or Zones. This means that Azure does not patch VMs that are part of an Availability Set or Zone at the same time, but one after the other based on the existing availability criteria. This option is particularly useful for Azure VMs that contain productive workloads and are operated in Availability Sets in Azure.
Windows automatic updates
This setting takes over the settings on the operating system level that are configured e.g. locally or via group policy.
Manual updates
This setting can be specified if there is another solution for maintaining system updates on the VM.
Image default
Can only be configured for Linux VMs.
How Azure Update Manager interact with the VM
The Azure Update Manager solution interact with the machine via a Extension which is called “WindowsOSUpdateExtension“. This is extenstion is integrated into the VMagent on Azure machines.
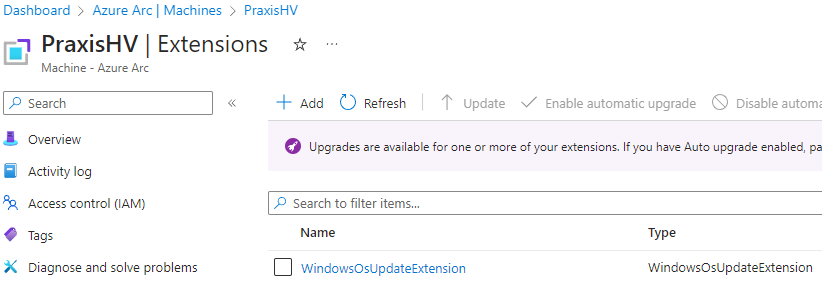
But on Azure Arc connected machines it can be found in the extension view. The Extension creates a log file in which you can read the various states and update assessments that are continously running on the VM.
This close this article and I will release the 3rd part in the next couple of days, where I will dive into the different features to manage update for different VMs with Update Manager.
Links
- Azure Update Manager overview
- Windows Update issues troubleshooting
- Azure virtual machine extensions and features
- We’re retiring the Log Analytics agent in Azure Monitor on 31 August 2024
- Microsoft Defender for Cloud – strategy and plan towards Log Analytics Agent (MMA) deprecation
- Automatic VM Guest Patching for Azure VMs
- Free Extended Security Updates only on Azure for Windows Server 2012 /R2and SQL Server 2012
- Update management center (preview) support matrix
- Azure Update Manager
- Azure Windows VM Agent overview
- Troubleshoot known issues with Azure Update Manager
- Automatic VM Guest Patching for Azure VMs – Azure Virtual Machines