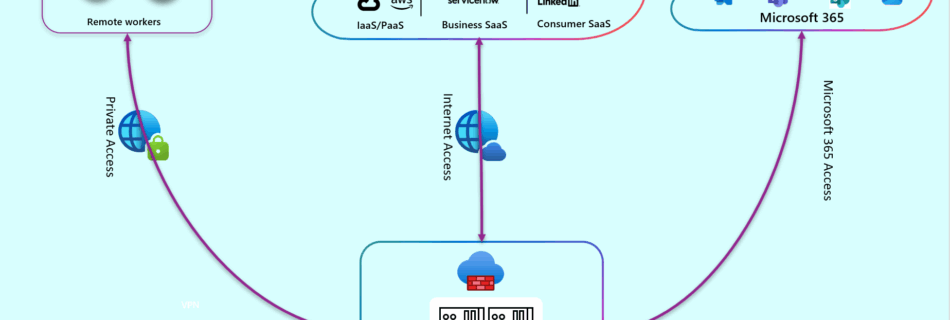
VPN, SSE, GSA, and Other Myths: Our MC2MC Connect Session on Navigating the New Networking Jungle
The modern enterprise network is changing faster than most organizations can keep up with. Traditional perimeters are dissolving, users are everywhere, applications live in multiple clouds, and security teams are expected to deliver seamless access without compromising control. In this jungle of acronyms and architectural shifts, it’s no surprise that many companies feel overwhelmed. That’s …