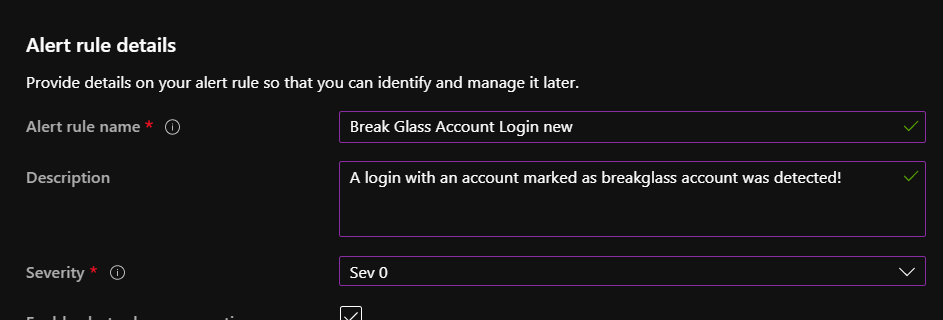
Howto setup and monitor Break Glass Accounts in your Tenant
09/07/2024 – Update 2 Microsoft enforce since 1st of July 2024 the need for Multifactor Authentication if a account access the Azure Portal. This also affects Break Glass accounts when the will use to access the Azure Portal. To reflect this new requirements classic Breakglass Accounts which only have a password enabled for login will …
Mehr über „Howto setup and monitor Break Glass Accounts in your Tenant“ Lesen