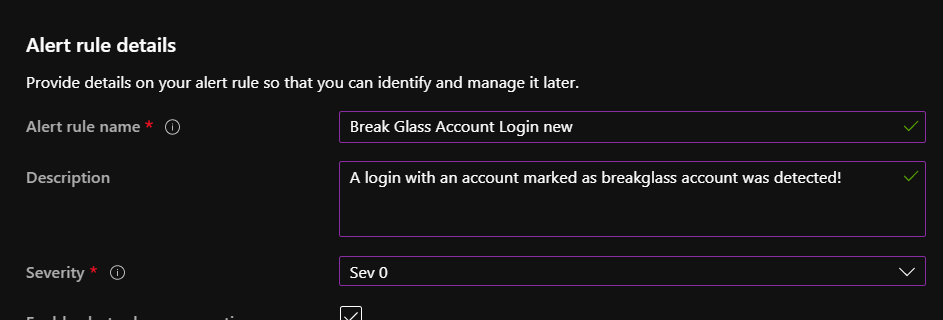
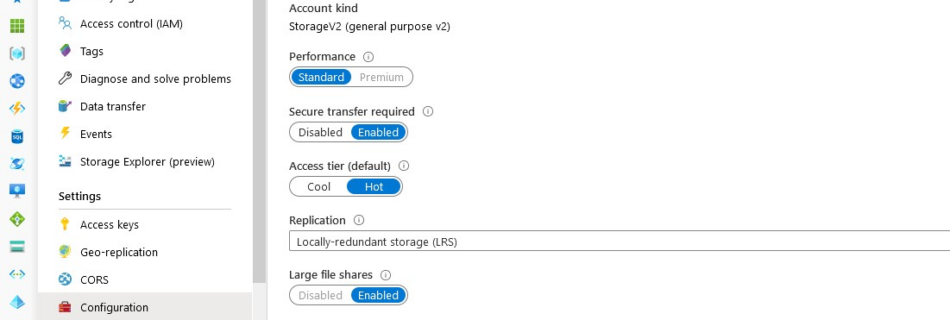
Speaking at WVD Tech Fest 2021 about Azure Files
Due do the covid pandamy, many organizations in Germany are in a challenging phase as many employees need to be given the opportunity to work from home. Many companies have not yet made this option available to their employees, or only to a few. Microsoft has created a new option with Windows Virtual Desktop to …
Mehr über „Speaking at WVD Tech Fest 2021 about Azure Files“ Lesen