Update 2
Please note: This article is replaced by All you need to know about Azure Files SMB authentication via Active Directory Domain Services.
Update 1
Azure Files on-premises Active Directory Domain Services authentication is since 11/06/20 GA. The article is upgraded and integrated the latest features and improvements.
12/06/20 Azure Files Hybrid PowerShell Module upgrate to v. 0.2.0
Update 2
In the past I had a lot of talks about Azure File Sync, a lightwight solutions to sync servers from different locations and branches via Azure Files. One often questions was, it is possible to use Azure Files directly with integrated on-premises Active Directory (AD DS) authentication – the great answer since a few days is Yes, this is possible.
Now you can use Azure Files with on-premises Active Directory authentication as a fully replacement for Fileservers. No need for Azure Active Directory Domain Services (Azure AD DS) or different settings on Azure Files. This gives great new ways to use Azure Files as an replacement for Windows based fileservers or for using as an profile store for Windows Virtual Desktop and come closer to a cloud native solution.
In this article I will explain how Azure files AD DS authentication works, how to configure it, some basic steps and more. Please feel free to use the comment section or Twitter to get in touch with me and give me feedback or ask questions.
[toc]
General
Region availability
Azure files are now GA and available in all public Azure regions.
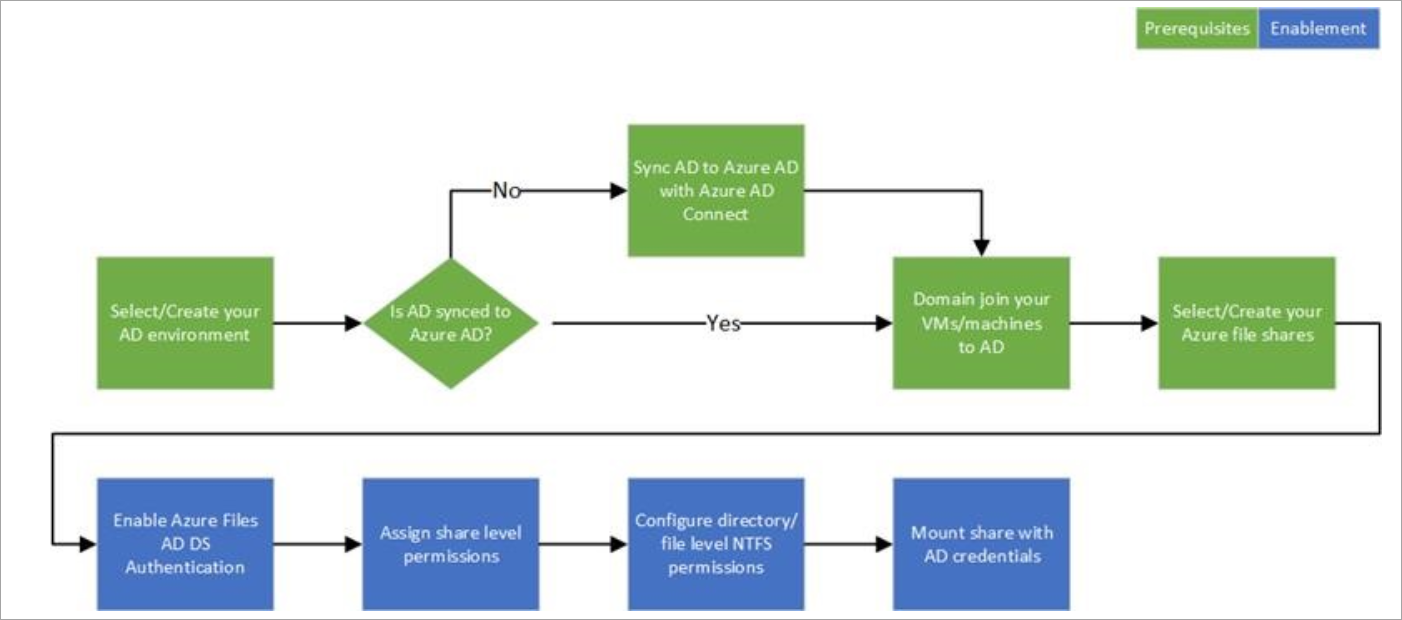
Requirements
To use Active Directory authentication for Azure Fileshares, there are some requirements:
- Existing Active Directory Domain Service (AD DS) on a Windows Server (doesn´t mean Azure AD DS)
- Identities used for access must be synced via Azure AD Connect to the Azure AD (same tenant as the Fileshare reside)
- Azure AD Tenant and the file share must be associate with the same subscription
- VM must be joined in the existing AD DS
- Use a region near by the VM from which you will access the Azure Fileshare (for best performance and lowest latency)
- Is only supported on machines newer then Windows 7 / WS2008R2 (EoL)
- Azure Files PowerShell Modul
- Needs Az module 2.0.0+ and Az.Storage 1.8.2-preview+
- The Client must be domainjoined to use the module
- The account must have permissions to create computer accounts or service accounts in the domain/OU
- No support for Computer accounts
- Only available from a single forest – for multi forest proper trust model must configured
Keep in mind, it`s only possible to use one authentication provider for a Azure Fileshare – Azure AD Domain Services (Azure AD DS) or Active Directory Domain Services (AD DS).
Recommendations
- Use separate Storage Accounts for Azure Fileshare AD authentication
- Create an separate OU for Azure Fileshare AD authentication in AD DS
For best practice it is useful to use separate Storage Accounts for Azure Files AD DS authentication, because with activation the fileshare will be a member of the the domain (this means in general the Storage Account join the domain). This mean all fileshares associated with the Storage account using AD DS authentication can`t use Azure AD authentication.
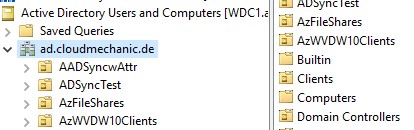
Each Domain uses GPO to enable settings for each OU in the Domain. To avoid issues for Storage Accounts (especially password issues) that will be member of the Domain, I recommend to create and use an separate OU for the Storage Accounts.
Please deactivate all GPOs on the OU that contains the Azure Fileshares, create a new GPO and set the password expiration for computer and service logon accounts to a maximum level or deactivate the expiration for the accounts inside the OU to avoid issues with Azure Files AD DS authentication.
Preparation
To use Azure Files with integrated SMB authentication, there is an additional Powershell module needed. This module are available for download at Azure Samples GitHub Page. Please use the latest one.
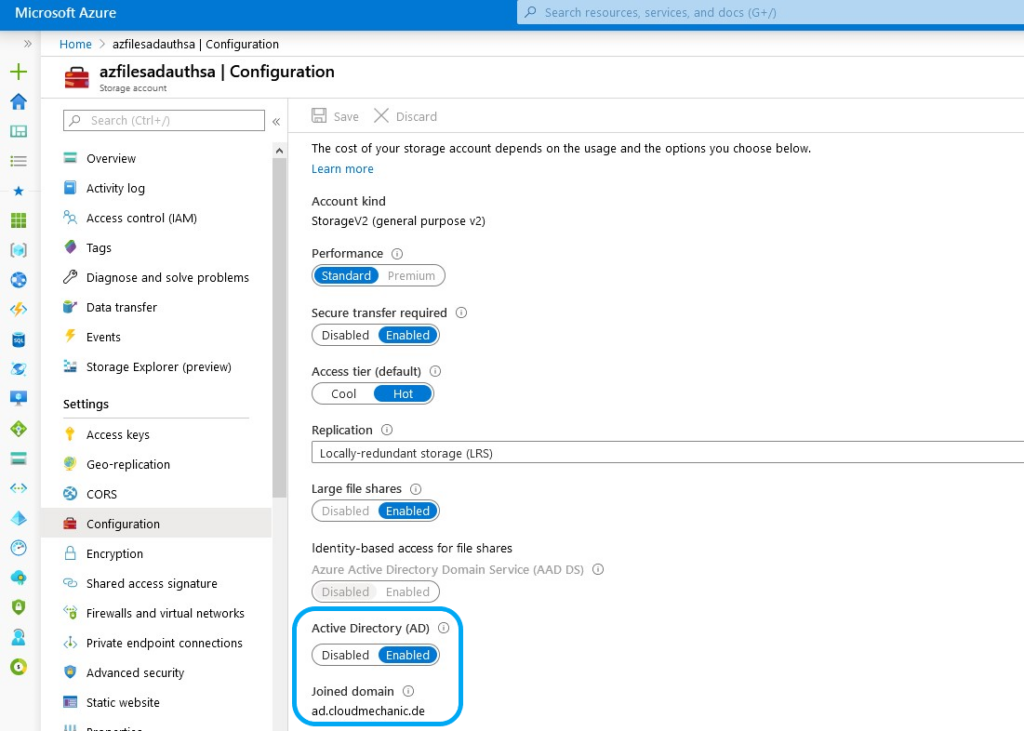
Enable Azure Files for AD authentication
To enable Azure Files for AD DS authentication there are some preparation steps needed. Please keep in mind he Storage Account join the domain as computer or service logon account:.
- Unzip the downloadad Zip Archiv AzFilesHybrid.zip
- [Optional] Create an OU for the Storage Accounts
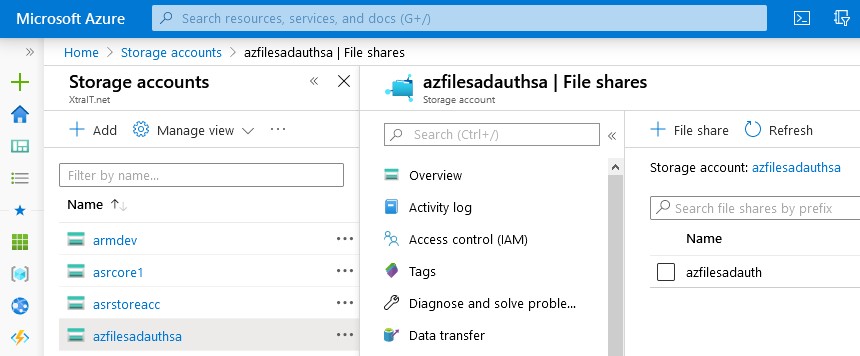
- Create a (separate) Storage Account in Azure
- Create a Azure file share in the Storage Account
- Start a evalated PowerShell Session with rights to create computer and service accounts in the domain on a domain member client
- Run the following powershell commands
- green = optional
- red = important
#Change the execution policy to unblock importing AzFilesHybrid.psm1 module
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope Currentuser
#Navigate to where AzFilesHybrid is unzipped and stored and run to copy the files into your path .\CopyToPSPath.ps1
#Import AzFilesHybrid module
Import-Module -name AzFilesHybrid
#Login with an Azure AD credential that has either storage account owner or contributer RBAC assignment
Connect-AzAccount
#Select the target subscription for the current session Select-AzSubscription -SubscriptionId "<your-subscription-id-here>"
#Register the target storage account with your active directory environment under the target OU
join-AzStorageAccountForAuth -ResourceGroupName "<resource-group-name-here>" -Name "<storage-account-name-here>" -DomainAccountType "<ServiceLogonAccount|ComputerAccount>" -OrganizationUnitName "<ou-name-here>"
Here are an short code example:
join-AzStorageAccountForAuth -ResourceGroupName "Storage_rg" -Name "azfilesadauthsa" -DomainAccountType "ComputerAccount" -OrganizationalUnitName "AzFileShares"

When using the correct permissions the storage account will join the domain as an Computer | Service logon object and the following message will shown.
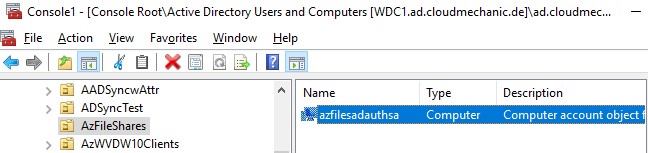
Keep an eye on the OU that are indicated for joining and the result will be a new computer object with the name of the storage account.
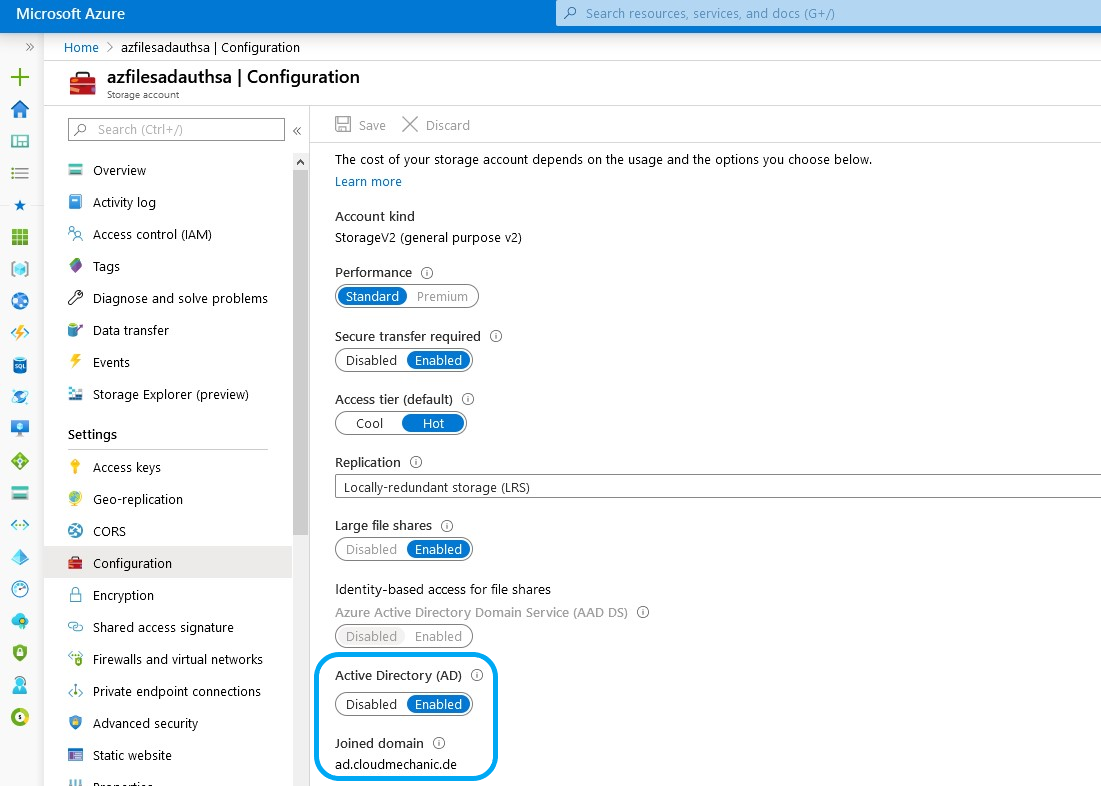
With this steps the feature for AD DS authentication for Azure fileshares are enabled.
Now it´s useful to define the initial permissions from the Azure AD portal. This is explained in the article Why Azure AD RBAC roles are needed for Active Directory File share authentication.
Pingback:WVD Weekly newsletter 30th March–5th April 2020 - Virtualmanc.co.uk
Hello,
When I run the CMDlet Join-AzStorageAccountForAuth, I alway get the following error: new-adcomputer a required attribute is missing
Do you know why?
Thank you and kind regards
Hi Ella,
can you share a screenshot about the error? Did you integrate the parameter „-DomainAccountType „ComputerAccount“?
Greetings
Gregor
Is this resolved , we are also facing the same error
Hi Satish, did you try to add the parameter -DomainAccountType “ComputerAccount” ?
Greetings
Gregor
I am setting up Azure files with on-premise AD permissions, When I run AZfiles hybrid command In PowerShell I get an error.
“Cannot validate argument on parameter ‚ActiveDirectoryDomainSid‘. The argument is null or empty. Provide an argument that is not null or empty, and then try the command again.
I am setting up Azure files with on premise AD permissions, When I run AZfiles hybrid command In powershell I get an error. Command is join-AzStorageAccountForAuth -ResourceGroupName $ResourceGroupName -Name $StorageAccountName -DomainAccountType „ComputerAccount“ -OrganizationUnitName „AzFileShares“ Error is “Cannot validate argument on parameter ‚ActiveDirectoryDomainSid‘. The argument is null or empty. Provide an argument that is not null or empty, and then try the command again.
Hi Naveen, did you use an account with Owner or Contributor permission at the Storage Account and is the account Domainjoind and synced to Azure AD via AAD Connect?
Thank you for this great write up!
I followed and my Azure File Share now shows Active Directory Domain Services and I see my computer account in the OU that I identified in PowerShell.
I am not able to successfully authenticate to the file share when I try to access it via UNC path and it’s private IP address. I can still access it via the public link
Hi Steve,
thanks for reach me. Did you get an error message or only the windows error message?
Have you tried different accounts, perhaps a privileged account to rule out missing permissions?
Greetings
Gregor
Hi Gergor,
Thanks for the write up.
I have totally different environment.
I have On premise Active Directory with a Sync to Azure AD
ex: contoso.com
And Iam using azure adds
for Ex: adds.contoso.com, I have configured Azure File share using the adds.contoso.com domain , we have a storage account created in the OU for authentication, I have a cloud only security Group created and added few users in it and same security group has RBAC permissions on Azure files.
Now I have Vm’s joined to adds.contoso.com , from this machines I logged in using the user1@contoso.com but Iam unable to access the share.
Any help please.
Hi Kharni,
Is user1 synced from local AD DS to Azure AD DS?
Have you tried to access the file share with an account directly from Azure AD DS and set the permission here to Storage File Data SMB share elevated contributor?
Greetings
Gregor
Join-azstorageaccount – gives the below error
New-ADComputer : The attribute syntax specified to the directory service is invalid
ActiveDirectoryServer:8203,Microsoft.ActiveDirectory.Management.Commands.NewAD
Computer
Hi Akella, does the error message still exist? Can you share a screenshot? Maybe we can look over it together.